



How toLifehacksModern livingLifehackTechnology
AI Pay My Bills: A Quick and Easy Lifehack for Splitting Receipts
read more
Artificial intelligenceEveryday aiItLifehacksMachine learningModern livingTechnology
Personal
Child’s Wishlist Games & Digital Gift Cards Roblox Gift Card – £10 (UK) - £10–£30 - Redeem for Robux or items in Fashion Famous / Royal High — they’ll enjoy picking exactly what she wants.
read more
Tech solutions
The problem with removing Nagios scheduled downtime When you schedule downtime for all services of a host, there’s a Nagios button for that.
read more
Lifehacks
Paying it forward to yourself One concept I try to carry with me is the concept of three selves.
read more
How toTech solutions
After much trawling of the Internet I found an interesting take on the pain of moving a Sharepoint page from one site to another, using Power Automate.
read more
Tech solutions
A post on tiktok where a young lad responded to a commenter “Why do you put your pronouns when you’re cis gender” made way too much sense.
read more
Tech solutions
Passwords are weak, we know this and so often methods such as key based authentication is used for connections like SSH.
read more
LinuxTech solutionsUbuntu
After banging my head against this problem from a different server, as WSL is not there yet for running as personal production services, I finally managed to hit the right keywords to google fu the answer.
read more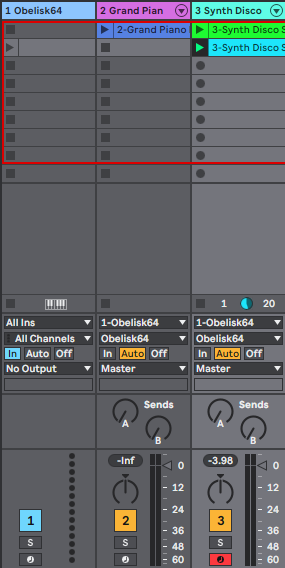
AbletonMusic
So when using the Frozen Plains Obelisk plugin in Ableton live 10 (I’m running10.
read more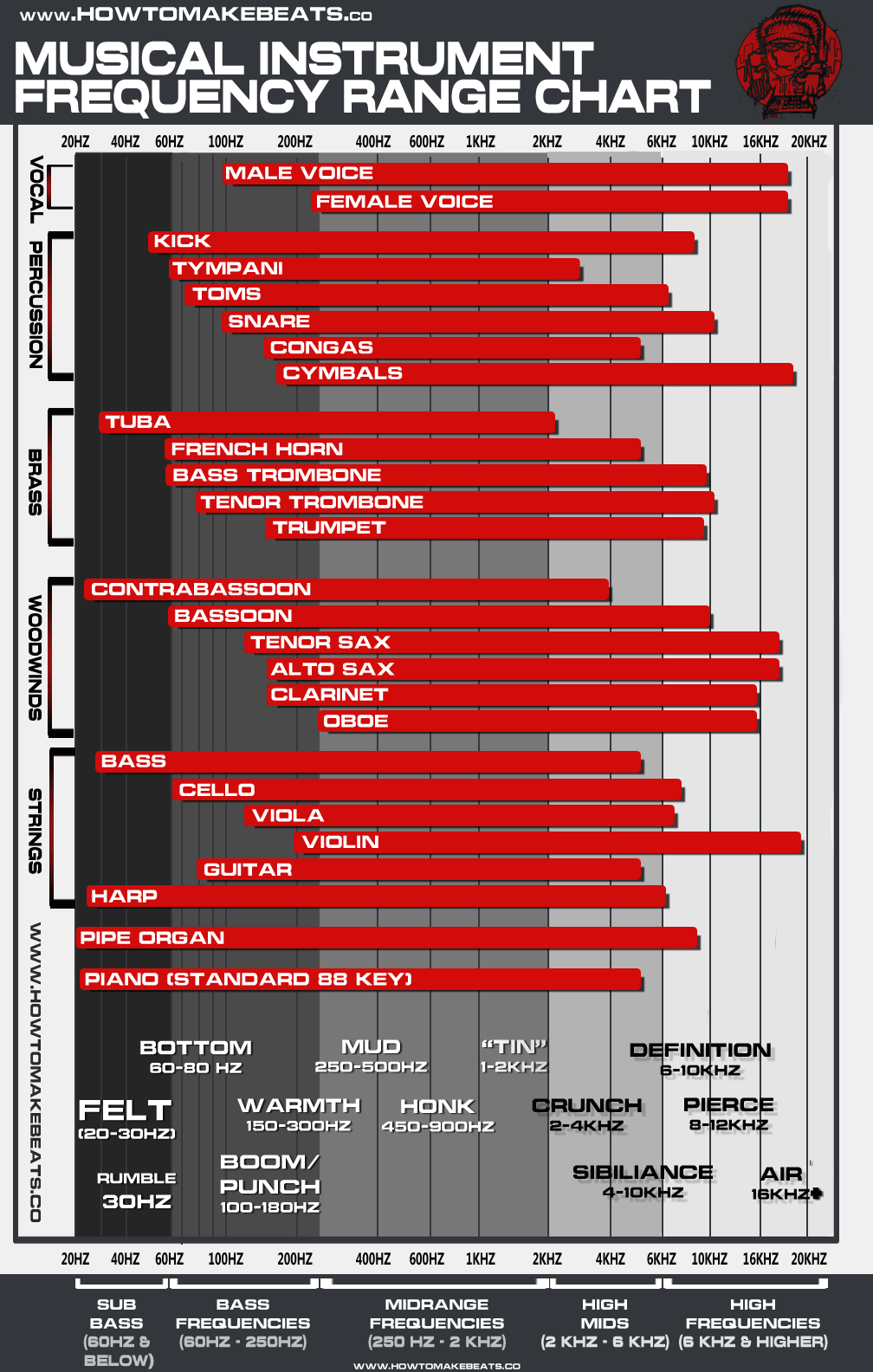
AbletonMusic
It looks like the original website is now unavailable and so I’m posting this here to share as the only other place it’s online it bloody Pinterest
read more
How toTech solutions
Use the following one liner to check the a certificate chain in detail:
read more
How toTech solutions
Run the following shell command to add all installed syntax files to your .
read more
Tech solutions
Add the following to your /etc/rkhunter.conf file #Config to add byobu files to your allow list ALLOWHIDDENDIR=/dev/shm/byobu-*-?
read more
Tech solutions
You could check for the existence of /var/run/reboot-required just to see if a reboot is needed but it’s more useful to check the existence and contents of /var/run/reboot-required.
read more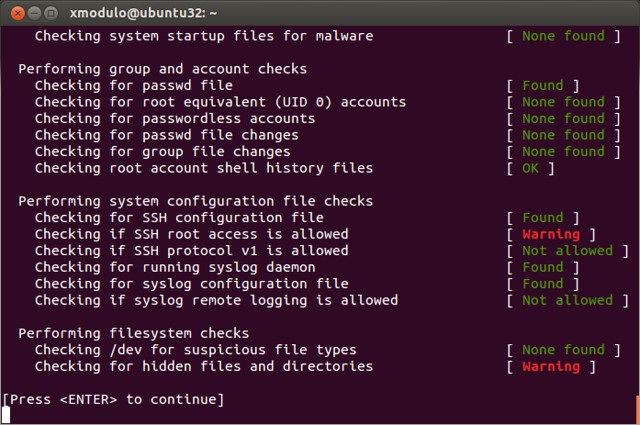
Tech solutions
I was trying to get this working by configuring the MAIL_CMD like so: echo -e “Subject: [rkhunter] Warnings found for ${HOST_NAME}\n\n” $(egrep -x “^[.
read more
Tech solutions
To make Byobu default on your local machine Byobu-enable only currently modifies your .
read more
Tech solutions
This will be a continually updated list of my favourite Linux CLI tools
read more
Tech solutions
UK Number: 020 7365 9792 or Freephone: 0800 587 1102
read more
Personal
Please be extremely wary of the company https://www.raidmart.com/
read more
CentosLinuxTech solutions
This post was an absolute life save, Yum was being blocked by our application aware firewall Palo Alto
read more